r00t.cz
Solution to www.canyoucrackit.co.uk
This is my complete walkthrough for http://www.canyoucrackit.co.uk/ GCHQ puzzle:
[NEW!] canyoufindit.co.uk GCHQ 2013 puzzle solution is here
Stage 1/3
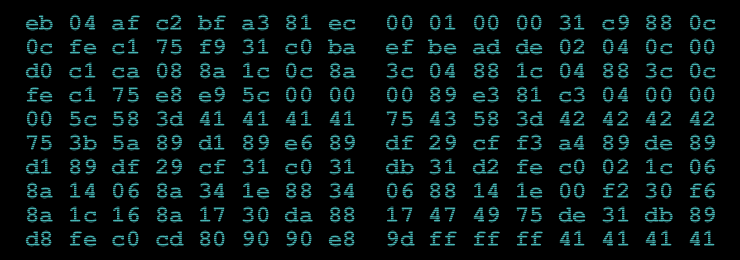
- Download the PNG with hex numbers and type them to create binary file.
This is first part and it's meant to be executed (it's x86 32bit code).
eb 04 af c2 bf a3 81 ec 00 01 00 00 31 c9 88 0c 0c fe c1 75 f9 31 c0 ba ef be ad de 02 04 0c 00 d0 c1 ca 08 8a 1c 0c 8a 3c 04 88 1c 04 88 3c 0c fe c1 75 e8 e9 5c 00 00 00 89 e3 81 c3 04 00 00 00 5c 58 3d 41 41 41 41 75 43 48 3d 42 42 42 42 75 3b 5a 89 d1 89 e6 89 df 29 cf f3 a4 89 de 89 d1 89 df 29 cf 31 c0 31 db 31 d2 fe c0 02 1c 06 8a 14 06 8a 34 1e 88 34 06 88 14 1e 00 f2 30 f6 8a 1c 16 8a 17 30 da 88 17 47 49 75 de 31 db 89 d8 fe c0 cd 80 90 90 e8 9d ff ff ff 41 41 41 41
- Second part is in "iTXt" chunk of PNG, base64 encoded. Decode it and append to first part.
1st part ends with "AAAA" marker, 2nd part starts with "BBBB".
iTXt chunk data: QkJCQjIAAACR2PFtcCA6q2eaC8SR+8dmD/zNzLQC+td3tFQ4qx8O447TDeuZw5P+0SsbEcYR78jKLw==
- Run the shellcode. On windows, I converted it to inline asm in form of
__asm __emit 0xEB; __asm __emit 0x04; ...etc...
- Or you can just find any exe and copy bytes at entry point.
- Run in debugger, add breakpoint just before INT 0x80 call.
Decrypted text will be placed on stack:
GET /15b436de1f9107f3778aad525e5d0b20.js HTTP/1.1
- Description of what shellcode does:
This is RC4 decoder with key set to 0xDEADBEEF. TEXT chunk data format is:
<magic 'BBBB'><encrypted length - 4byte word><encrypted bytes...>
- Download this JS file for stage 2
Stage 2/3
- You can get JS here: 15b436de1f9107f3778aad525e5d0b20.js
- File is pretty self-explanatory. Just write the code to emulate VM, no secrets there.
- When you run it and reach HLT instruction, memory will contain:
000: 31 04 33 AA 40 02 80 03 52 00 72 01 73 01 B2 50 << 1st decryption code 010: 30 14 C0 01 80 00 10 10 00 00 00 00 00 00 00 00 020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 090: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0A0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0B0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0C0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0D0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0E0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0F0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 100: 32 00 75 0C 31 08 33 32 40 02 80 03 52 00 72 01 << 2nd decryption code 110: 73 03 B2 00 C3 B0 00 30 1B C0 01 FF 00 00 00 00 (decrypted by 1st one) 120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 130: 00 00 75 10 01 00 00 00 00 00 00 00 00 00 00 00 140: CC 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 150: 7D 1F 15 60 4D 4D 52 7D 0E 27 6D 10 6D 5A 06 56 << Unknown data block 160: 47 14 42 0E B6 B2 B2 E6 EB B4 83 8E D7 E5 D4 D9 170: C3 F0 80 95 F1 82 82 9A BD 95 A4 8D 9A 2B 30 69 180: 4A 69 65 55 1C 7B 69 1C 6E 04 74 35 21 26 2F 60 190: 03 4E 37 1E 33 54 39 E6 BA B4 A2 AD A4 C5 95 C8 1A0: C1 E4 8A EC E7 92 8B E8 81 F0 AD 98 A4 D0 C0 8D 1B0: AC 22 52 65 7E 27 2B 5A 12 61 0A 01 7A 6B 1D 67 1C0: 47 45 54 20 2F 64 61 37 35 33 37 30 66 65 31 35 << Solution ASCII text 1D0: 63 34 31 34 38 62 64 34 63 65 65 63 38 36 31 66 (decrypted by 2nd code) 1E0: 62 64 61 61 35 2E 65 78 65 20 48 54 54 50 2F 31 1F0: 2E 30 00 00 00 00 00 00 00 00 00 00 00 00 00 00 200: 37 7A 07 11 1F 1D 68 25 32 77 1E 62 23 5B 47 55 << Another unknown block 210: 53 30 11 42 F6 F1 B1 E6 C3 CC F8 C5 E4 CC C0 D3 220: 85 FD 9A E3 E6 81 B5 BB D7 CD 87 A3 D3 6B 36 6F 230: 6F 66 55 30 16 45 5E 09 74 5C 3F 29 2B 66 3D 0D 240: 02 30 28 35 15 09 15 DD EC B8 E2 FB D8 CB D8 D1 250: 8B D5 82 D9 9A F1 92 AB E8 A6 D6 D0 8C AA D2 94 260: CF 45 46 67 20 7D 44 14 6B 45 6D 54 03 17 60 62 270: 55 5A 4A 66 61 11 57 68 75 05 62 36 7D 02 10 4B 280: 08 22 42 32 BA E2 B9 E2 D6 B9 FF C3 E9 8A 8F C1 290: 8F E1 B8 A4 96 F1 8F 81 B1 8D 89 CC D4 78 76 61 2A0: 72 3E 37 23 56 73 71 79 63 7C 08 11 20 69 7A 14 2B0: 68 05 21 1E 32 27 59 B7 CF AB DD D5 CC 97 93 F2 2C0: E7 C0 EB FF E9 A3 BF A1 AB 8B BB 9E 9E 8C A0 C1 2D0: 9B 5A 2F 2F 4E 4E 00 00 00 00 00 00 00 00 00 00 2E0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 2F0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
- VM code does this:
for(i=0;i<80;i++) mem[0x100+i]^=i+0xAA; for(i=0;i<51;i++) mem[0x1C0+i]^=i*3+0x32;
- Stage 2 solution text is:
GET /da75370fe15c4148bd4ceec861fbdaa5.exe HTTP/1.0
- Unknowns:
There are still some encrypted blocks of memory that looks suspicious.
Because both decryption routines used XOR pattern in form of i*X+Y, I have
tried bruteforcing decoding for these unknown parts as well.
See end of page for more details.
Stage 3/3
- Exe file is here, together with needed CYGWIN dlls: da75370fe15c4148bd4ceec861fbdaa5.zip
- After quick inspecion, this executable loads license.txt that have following format:
<4 byte magic><8byte password><4byte word1><4byte word2><4byte word3>
- First bytes of file (magic) must be gchq.
- Then Exe does unix CRYPT hash with hqDTK7b8K2rvw salt of the 8 byte password,
result must match hqDTK7b8K2rvw. But you can easily NOP this check
at 0x0040119C and everything will still work fine. - Another way is to bruteforce this hash, solution is cyberwin.
- Exe then does GET request to server in following format:
GET /hqDTK7b8K2rvw/%x/%x/%x/key.txt
- HEX numbers are the words 1,2,3 from license file.
- There is small hint where to find these, exe prints to console:
loading stage1 license key(s)... loading stage2 license key(s)...
- where at stage1 it reads one word, in stage2 two words.
- In stage 1 code, just at beginning, EB 04 instruction skips over 4 bytes.
This is the key for first stage: 0xa3bfc2af - For stage 2, in JS code is unused variable firmware with values 0xd2ab1f05, 0xda13f110.
- So complete license.txt file in HEX is:
67 63 68 71 63 79 62 65 72 77 69 6E AF C2 BF A3 05 1F AB D2 10 F1 13 DA 61
- This translates to:
GET /hqDTK7b8K2rvw/a3bfc2af/d2ab1f05/da13f110/key.txt HTTP/1.0
- Server returns:
Pr0t3ct!on#cyber_security@12*12.2011+
- Note that running EXE will not do proper request to server, so you will have to copy
the URL to browser. This is due to not including "Host:" header in request. - When you use this on main page, you get redirected to:
http://canyoucrackit.co.uk/soyoudidit.asp with following text:
So you did it. Well done! Now this is where it gets interesting. Could you use your skills and ingenuity to combat terrorism and cyber threats? As one of our experts, you'll help protect our nation's security and the lives of thousands. Every day will bring new challenges, new solutions to find – and new ways to prove that you're one of the best.
- This was fun to do, don't you think?
The end? Maybe not

There are speculations that this simple solution is just some form of honeypot.
First HTTP get was with HTTP/1.1, but later it's HTTP/1.0.
Then there are unused bytes in VM memory.
- I have checked all images on web page, no other hidden data except the base64 chunk
in PNG file. - Part of memory after VM is run:
100: 32 00 75 0C 31 08 33 32 40 02 80 03 52 00 72 01 110: 73 03 B2 00 C3 B0 00 30 1B C0 01 FF 00 00 00 00 120: 130: 00 00 75 10 01 00 00 00 00 00 00 00 00 00 00 00 140: CC 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
- Note the similarity of these blocks. What I think this means is you should mix these
together in some way to create new decryption VM instructions to continue.
But tried XORing or replacing non-zero bytes... no luck. Also the 3 blocks seems to be RC4 encrypted.Probably not, see below. They all share same key, this
can be seen on MSB bits of cryptext. Data blocks are all 112 bytes long
at offsets 0x150, 0x200, 0x270.
Tried the firmware values and also 0xDEADBEEF without getting anything useful.
3 Blocks may decrypt to 3 ASCII HEX words needed for licence.txt to get right server reply.- See the graphical interpretation of these binary blocks on right ------------------------------------------->
You can see MSB bits are same for all blocks, as expected if result is ASCII text. - This MSB pattern seems to be too periodic, this this isn't using RC4. It looks more like
XOR i*X+Y pattern we seen for decrypting code and URL.
- One solution (that makes all MSB bits zero as expected for ASCII text) is this:
for(i=0;i<112;i++) mem[0x150+i]^=i*5+31; for(i=0;i<112;i++) mem[0x200+i]^=i*5+31; for(i=0;i<112;i++) mem[0x270+i]^=i*5+31;
- One firmware value is 0xd2ab1f05 = 1F=31 05=5 -> values for above algorithm. Coincidence?
- This is the result:
b;<N~uo?Ik<F6:c<(`;p5:?t|("(|Uac|4I["Z_xZyU{a+5cE}|K?SD.Y85sjvz:\*^p@,Dd=83;?e0bnP3R$ZF:V,L~O 5wS&[km?6x5M;7A+X-(^.?,%Ugu;O4x;"?<Dh<uy<tTPYcO|ui:9S-5YhY0!vU(k3e`rL.5ms;C`~o`6hW]TA[fqh_k4smCk}{$a;gY9_y?z76gZ'n0AOi3eY6Li\b8W%(J~cHR)j*2I3`&bu!gV;L9j4pA%^eB::{0%qjE)RcVax:/xsk}*.=u[\KT@IWk9/N7aHpA_$5H'LCW76XHtRA*krs|WZxu|U;d^&!]V
Formated to 3 lines, for 0x150, 0x200 and 0x270 block contents. It may or may not be single block. Ctrl-C safe.
- It's not really readable, but all characters are in printable range 0x20-0x7F.
I found it to get MSB bits zero, but it also produced just printable characters!
This looks interesting. - From 96 characters in range 0x20 - 0x7F are all used except: 0x23 0x31 0x3E 0x47 0x51 0x6C 0x7F
There is total 90 unique characters... base 90 code? - Converted this block from base 96 to base 16 and used ent entropy analyzer program on this data:
Entropy = 7.133685 bits per byte. Optimum compression would reduce the size of this 273 byte file by 10 percent. Chi square distribution for 273 samples is 288.70, and randomly would exceed this value 7.21 percent of the times. Arithmetic mean value of data bytes is 127.7070 (127.5 = random). Monte Carlo value for Pi is 3.022222222 (error 3.80 percent). Serial correlation coefficient is 0.014271 (totally uncorrelated = 0.0).
- Same for base 90 to base 16:
Entropy = 7.284051 bits per byte. Optimum compression would reduce the size of this 269 byte file by 8 percent. Chi square distribution for 269 samples is 219.21, and randomly would exceed this value 94.91 percent of the times. Arithmetic mean value of data bytes is 126.8067 (127.5 = random). Monte Carlo value for Pi is 3.090909091 (error 1.61 percent). Serial correlation coefficient is 0.040349 (totally uncorrelated = 0.0).
- Is this just a random fill to put something in memory?
All content on this webpage is published for personal use only.
You are using any software downloaded from this page at your own risk. Some software may be illegal to use in your country.
© r00t 2009-2021 (email: r00t@<this domain>)