r00t.cz
Solution to canyoufindit.co.uk GHCQ
This is my complete walkthrough on how to solve https://canyoufindit.co.uk/ GCHQ puzzle:
THIS PAGE CONTAINS SPOILERS, DON'T READ IT IF YOU WANT TO COMPLETE THE PUZZLE BY YOURSELF!!!
Step 1/5
- You are presented with:
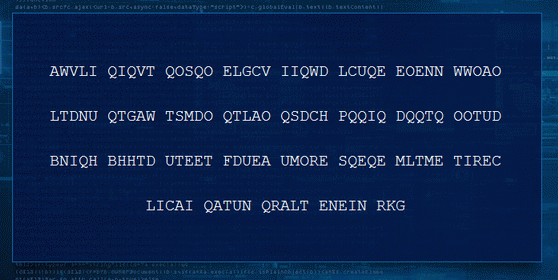
- Text from image:
AWVLI QIQVT QOSQO ELGCV IIQWD LCUQE EOENN WWOAO
LTDNU QTGAW TSMDO QTLAO QSDCH PQQIQ DQQTQ OOTUD
BNIQH BHHTD UTEET FDUEA UMORE SQEQE MLTME TIREC
LICAI QATUN QRALT ENEIN RKG
- Remove spaces and reorder the text into lines 14 characters long.
Read the letters in columns, from top to bottom for each column starting from left side. Q character acts as a SPACE.
AWVLIQIQVTQOS
QOELGCVIIQWDL
CUQEEOENNWWOA
OLTDNUQTGAWTS
MDOQTLAOQSDCH
PQQIQDQQTQOOT
UDBNIQHBHHTDU
TEETFDUEAUMOR
ESQEQEMLTMETI
RECLICAIQATUN
QRALTENEINRKG
- Result:
A COMPUTER WOULD DESERVE TO BE CALLED INTELLIGENT IF IT COULD DECEIVE A HUMAN INTO BELIEVING THAT IT WAS HUMAN WWW.METRO.CO.UK/TURING
- Keyword answer: Turing
Step 2/5
- Download the comp1.key, it's standard PEM private key:
-----BEGIN RSA PRIVATE KEY-----
MIIC2gIBAAKBgDfABK8+joDLdbFTDJ+y3PTTzkqCi1L2qEjgxdg1iyZshJTeKUck
SYVyKBeOBtB3FwwqXVa6iNEHJeLFewFE6ulEOIcatVp11Zg0ibMfnqTivbd6t8/z
3KzqrFksg9xQiicMactmTqFkm8ro5ODc2NTQzMjEwLy4tLCslBOCOVHxAgMBAAEC
gYATW12FB2BtQbecmSxh6rWjYENZRZhgdvoZS8oF9xlYfwdNtRF5/RR1/BwFia++
BAuBktgTu/KzORsjcNPzrd0uTCbTG6hW8YPK2ROVOOeAMHek8Nl3+SW5wdePKuWw
MdjDDjqxXDns+ZC1d2Cpz5V+x+2znOYL0bsEKei0sWl7LQKBgDfABK8+joDLdbFT
DJ+y3PTTzkqCi1L2qEjgxdg1iyZshJTeKUckSYVyKBeOBtB3FwwqXVa6iNEHJeLF
ewFE6uhVSior5HGPArFhsOQ0v9ob1NCV7P8M99qN4XplmX/xs05HgQCVh9aMWtio
pKCcmJSQjIiEgHx4dHBsU9JB+TvkAkB3dy53aHRzaXNpbGd1b2VjdHNyZWhzcmku
ZW9jdS4va2xidGVoY2VsIHkgICAgICAgICAgICAgICAgICAgIAuPAkATpSSd/C5S
IEAbUPk+ZYAdt7OYVzay7ViAiaukhkt+/sJG+m8GmHnAKyLf9ohx3/aIcd/2iHHf
9ohx3/ayirJPAkAIefJYEpdAoRjJQCHPGUpOVjLiyQMyPcnsutG+ctAGGU8lZTDU
yUim9V7iwqTE4sKkxOLCpMTiwqTE4sKkxOFNAoGAFInzTsAOkauW3crd1XfxMhxi
tUkapdQqlwvFhZuouNIybfEOfW6WkjtghBDyqf50cEFWXMJ7Vk8mr6cwTosPvYKU
VXKUCblretLTeU95TlbkprizPky++5b7pQuSi3mpLMi+6VgvcjTthfXPYNg2JjJp
gmteC4felYL/2FTAmT8=
-----END RSA PRIVATE KEY-----
- Use OpenSSL to analyze it (openssl.exe pkey -in comp1.key -text):
- Or you can just paste the Base64 encoded characters to http://i-tools.org/base64, select "Download result" option and click Decode.
modulus:
37:c0:04:af:3e:8e:80:cb:75:b1:53:0c:9f:b2:dc:
f4:d3:ce:4a:82:8b:52:f6:a8:48:e0:c5:d8:35:8b:
26:6c:84:94:de:29:47:24:49:85:72:28:17:8e:06:
d0:77:17:0c:2a:5d:56:ba:88:d1:07:25:e2:c5:7b:
01:44:ea:e9:44:38:87:1a:b5:5a:75:d5:98:34:89:
b3:1f:9e:a4:e2:bd:b7:7a:b7:cf:f3:dc:ac:ea:ac:
59:2c:83:dc:50:8a:27:0c:69:cb:66:4e:a1:64:9b:
ca:e8:e4:e0:dc:d8:d4:d0:cc:c8:c4:c0:bc:b8:b4:
b0:ac:94:13:82:39:51:f1
- Modulus is XORed with ((128-byte_index)*4+0x90)&0xFF sequence and decoded results in:
A7 4C 8C 2B BE F2 F8 BF 05 DD 3B 68 FF EE 84 A0
83 82 02 C6 CB 6E CE 9C 78 CC ED FC 15 97 3E 78
94 98 D6 2D 47 D8 B1 71 82 C4 FF 6A E6 0C AF C3
DC E6 95 92 7A 34 69 B3 95 4E 6D DF A1 D8 72 7D
D4 B4 0F 9E 35 26 0D A1 E8 58 E1 D7 7F C2 FC B6
ED FB 32 F3 8F CF E4 98 DA 80 71 08 A3 C0 48 9E
37 00 61 CF 66 B2 59 90 6B 26 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 3C B7 22 A5 C9 65
privateExponent:
13:5b:5d:85:07:60:6d:41:b7:9c:99:2c:61:ea:b5:
a3:60:43:59:45:98:60:76:fa:19:4b:ca:05:f7:19:
58:7f:07:4d:b5:11:79:fd:14:75:fc:1c:05:89:af:
be:04:0b:81:92:d8:13:bb:f2:b3:39:1b:23:70:d3:
f3:ad:dd:2e:4c:26:d3:1b:a8:56:f1:83:ca:d9:13:
95:38:e7:80:30:77:a4:f0:d9:77:f9:25:b9:c1:d7:
8f:2a:e5:b0:31:d8:c3:0e:3a:b1:5c:39:ec:f9:90:
b5:77:60:a9:cf:95:7e:c7:ed:b3:9c:e6:0b:d1:bb:
04:29:e8:b4:b1:69:7b:2d
- Doesn't seems to be encoded in any obvious way
prime1:
37:c0:04:af:3e:8e:80:cb:75:b1:53:0c:9f:b2:dc:
f4:d3:ce:4a:82:8b:52:f6:a8:48:e0:c5:d8:35:8b:
26:6c:84:94:de:29:47:24:49:85:72:28:17:8e:06:
d0:77:17:0c:2a:5d:56:ba:88:d1:07:25:e2:c5:7b:
01:44:ea:e8:55:4a:2a:2b:e4:71:8f:02:b1:61:b0:
e4:34:bf:da:1b:d4:d0:95:ec:ff:0c:f7:da:8d:e1:
7a:65:99:7f:f1:b3:4e:47:81:00:95:87:d6:8c:5a:
d8:a8:a4:a0:9c:98:94:90:8c:88:84:80:7c:78:74:
70:6c:53:d2:41:f9:3b:e4
- Prime1 is XORed with ((128-byte_index)*4+0x50)&0xFF sequence and decoded results in:
67 8C 4C EB 7E B2 B8 FF 45 9D 7B 28 BF AE C4 E0
C3 C2 42 86 8B AE 0E 5C B8 0C 2D 3C D5 57 FE B8
54 58 16 ED 87 98 F1 31 C2 84 BF 2A A6 4C EF 83
9C A6 D5 D2 3A F4 A9 73 55 8E AD 1F 61 18 B2 BC
05 06 62 6F A4 4D B7 36 81 4D 98 C0 14 A3 C2 0F
C4 DC 9D E8 FF F0 0F 2E 7D 0D 92 81 79 A3 29 67
9E 8B 49 C4 55 3B 6E 38 EA 74 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 3B B6 21 A5 63 B0
prime2:
77:77:2e:77:68:74:73:69:73:69:6c:67:75:6f:65:
63:74:73:72:65:68:73:72:69:2e:65:6f:63:75:2e:
2f:6b:6c:62:74:65:68:63:65:6c:20:79:20:20:20:
20:20:20:20:20:20:20:20:20:20:20:20:20:20:20:
20:20:0b:8f
- Prime2 section contains link www.thisisgloucestershire.co.uk/bletchley to stage 3 in plain ASCII, even/odd bytes swapped
- Keyword answer: Bletchley
exponent1:
13:a5:24:9d:fc:2e:52:20:40:1b:50:f9:3e:65:80:
1d:b7:b3:98:57:36:b2:ed:58:80:89:ab:a4:86:4b:
7e:fe:c2:46:fa:6f:06:98:79:c0:2b:22:df:f6:88:
71:df:f6:88:71:df:f6:88:71:df:f6:88:71:df:f6:
b2:8a:b2:4f
- Exponent1 is XORed with repeating 32bit pattern 88 71 DF F6 and decoded results in:
9B D4 FB 6B 74 5F 8D D6 C8 6A 8F 0F B6 14 5F EB
3F C2 47 A1 BE C3 32 AE 08 F8 74 52 0E 3A A1 08
4A 37 25 99 8E E9 A6 36 A3 53 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 3A FB 6D B9
exponent2:
08:79:f2:58:12:97:40:a1:18:c9:40:21:cf:19:4a:
4e:56:32:e2:c9:03:32:3d:c9:ec:ba:d1:be:72:d0:
06:19:4f:25:65:30:d4:c9:48:a6:f5:5e:e2:c2:a4:
c4:e2:c2:a4:c4:e2:c2:a4:c4:e2:c2:a4:c4:e2:c2:
a4:c4:e1:4d
- Exponent2 is XORed with repeating 32bit pattern A4 C4 E2 C2 and decoded results in:
AC BD 10 9A B6 53 A2 63 BC 0D A2 E3 6B DD A8 8C
F2 F6 00 0B A7 F6 DF 0B 48 7E 33 7C D6 14 E4 DB
EB E1 87 F2 70 0D AA 64 51 9A 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 03 8F
coefficient:
14:89:f3:4e:c0:0e:91:ab:96:dd:ca:dd:d5:77:f1:
32:1c:62:b5:49:1a:a5:d4:2a:97:0b:c5:85:9b:a8:
b8:d2:32:6d:f1:0e:7d:6e:96:92:3b:60:84:10:f2:
a9:fe:74:70:41:56:5c:c2:7b:56:4f:26:af:a7:30:
4e:8b:0f:bd:82:94:55:72:94:09:b9:6b:7a:d2:d3:
79:4f:79:4e:56:e4:a6:b8:b3:3e:4c:be:fb:96:fb:
a5:0b:92:8b:79:a9:2c:c8:be:e9:58:2f:72:34:ed:
85:f5:cf:60:d8:36:26:32:69:82:6b:5e:0b:87:de:
95:82:ff:d8:54:c0:99:3f
- Doesn't seems to be encoded in any obvious way
- There is quite a lot of data in this private key, but not sure if it's used for anything or if it's just filler.Binary blocks seems to have distinct format: <unknown binary><few zeroes><6-2 unknown bytes at the end>
Step 3/5
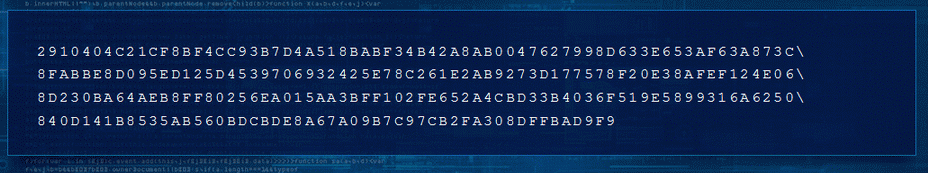
- Page with following text
2910404C21CF8BF4CC93B7D4A518BABF34B42A8AB0047627998D633E653AF63A873C\
8FABBE8D095ED125D4539706932425E78C261E2AB9273D177578F20E38AFEF124E06\
8D230BA64AEB8FF80256EA015AA3BFF102FE652A4CBD33B4036F519E5899316A6250\
840D141B8535AB560BDCBDE8A67A09B7C97CB2FA308DFFBAD9F9
- Let's try decrypting it with the parameters from PEM key file. You can use http://nmichaels.org/rsa.py online tool.
public modulus:
37 c0 04 af 3e 8e 80 cb 75 b1 53 0c 9f b2 dc
f4 d3 ce 4a 82 8b 52 f6 a8 48 e0 c5 d8 35 8b
26 6c 84 94 de 29 47 24 49 85 72 28 17 8e 06
d0 77 17 0c 2a 5d 56 ba 88 d1 07 25 e2 c5 7b
01 44 ea e9 44 38 87 1a b5 5a 75 d5 98 34 89
b3 1f 9e a4 e2 bd b7 7a b7 cf f3 dc ac ea ac
59 2c 83 dc 50 8a 27 0c 69 cb 66 4e a1 64 9b
ca e8 e4 e0 dc d8 d4 d0 cc c8 c4 c0 bc b8 b4
b0 ac 94 13 82 39 51 f1
private exponent:
13 5b 5d 85 07 60 6d 41 b7 9c 99 2c 61 ea b5
a3 60 43 59 45 98 60 76 fa 19 4b ca 05 f7 19
58 7f 07 4d b5 11 79 fd 14 75 fc 1c 05 89 af
be 04 0b 81 92 d8 13 bb f2 b3 39 1b 23 70 d3
f3 ad dd 2e 4c 26 d3 1b a8 56 f1 83 ca d9 13
95 38 e7 80 30 77 a4 f0 d9 77 f9 25 b9 c1 d7
8f 2a e5 b0 31 d8 c3 0e 3a b1 5c 39 ec f9 90
b5 77 60 a9 cf 95 7e c7 ed b3 9c e6 0b d1 bb
04 29 e8 b4 b1 69 7b 2d
text:
29 10 40 4C 21 CF 8B F4 CC 93 B7 D4 A5 18 BA BF 34 B4 2A 8A B0 04 76 27 99 8D 63 3E 65 3A F6 3A 87 3C 8F AB BE 8D 09 5E D1 25 D4 53 97 06 93 24 25 E7 8C 26 1E 2A B9 27 3D 17 75 78 F2 0E 38 AF EF 12 4E 06 8D 23 0B A6 4A EB 8F F8 02 56 EA 01 5A A3 BF F1 02 FE 65 2A 4C BD 33 B4 03 6F 51 9E 58 99 31 6A 62 50 84 0D 14 1B 85 35 AB 56 0B DC BD E8 A6 7A 09 B7 C9 7C B2 FA 30 8D FF BA D9 F9
- Select HEX format and click DECRYPT
Result:
0x20 0x20 0x20 0x20 0x20 0x20 0x20 0x20 0x77 0x77 0x2e 0x77 0x68 0x74 0x72 0x65 0x67 0x65 0x73 0x69 0x65 0x74 0x2e 0x72 0x6f 0x63 0x75 0x2e 0x2f 0x6b 0x6e 0x65 0x67 0x69 0x61 0x6d 0x30 0x32 0x33 0x31 0x20 0x20 0x20 0x20 0x20 0x20 0x20 0x20
- In ASCII: ww.whtregesiet.rocu./knegiam0231
- Bytes swapped: http://www.theregister.co.uk/enigma2013
- Keyword answer: Enigma2013
Step 4/5
- URL: http://www.theregister.co.uk/enigma2013
- Page contains one image:
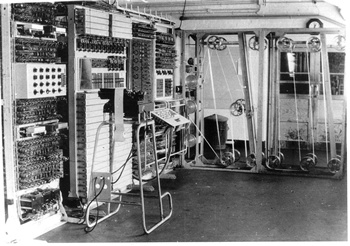
- After quick look inside, jpeg "JFIF" header is there twice, so there is 2nd JPEG image concatenated after the first one.
- You can use for example JPEGSnoop program for this. Load the JPG file, use Tools/Image Search Fwd, then Tools/Export JPEG and save it to new file.
- Extracted 2nd image is:

- Easy eh?! http://www.eveningstandard.co.uk/colossus
- Keyword answer: Colossus
Step 5/5

- Can also be found by simply googling "Take part in the latest challenge from GCHQ". Yes, that's quite stupid and one would expect pages like these to be excluded from search engines.
- Next time, GHCQ, your agents should try adding these pages to robots.txt :) This kind of spoils the fun with people directly linking to the final page...
- Keyword answer: Secured
Finish page
Just enter all the keywords to main page and you will be presented with:
Congratulations, you’ve found and solved every one of the codes we hid around the web. Submit your details below to enter our free prize draw.
- If you are unlucky enough to live in UK while still lucky enough to win, enjoy your RaspberryPI or new phone...
Summary
This years challenge wasn't quite that hard. Especially step #4. It could have been much more fun to let people use private key file to connect to some SSH server... that would be more interesting. Puzzle from the last year had that "write the virtual machine" part that took quite some time, but this year, almost all steps only required one simple idea and that was it.
All content on this webpage is published for personal use only.
You are using any software downloaded from this page at your own risk. Some software may be illegal to use in your country.
© r00t 2009-2021 (email: r00t@<this domain>)